DeconstruCTF Writeup
Intro
This past Friday and Saturday was Google’s DesconstruCTF, which is a capture the flag competition for teams and individuals around the world; it included challenges about web application exploitation, cryptography, OSINT, and more. This was my first timed CTF so I wasn’t too worried about completing a ton of challenges, I really just wanted to get in and see what I could do. In the end I wound up completing just one challenge, but I got pretty far in another. I’ll start by going over how I was able to complete that challenge, before I move on to where I struggled in the other challenges, and finish up by talking about my next steps.
Here's a Flag
This is the first challenge in the Web section. It focused on understanding the front-end of a web application.
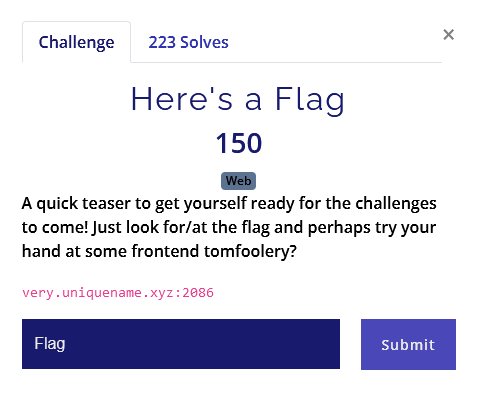
Above you can see the clue and the site where this flag is hidden. The first step is to go to the site and see what I’m working with.
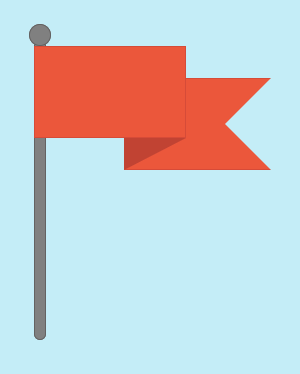
In this case, the entire page is just this CSS-built flag. The next step is to go into the CSS and take a quick look for clues.
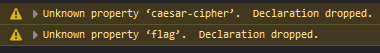
Upon looking in the console, there are these two unknown properties. Looking directly at the CSS text, the flag and caesar-cipher properties are pretty easy to find.
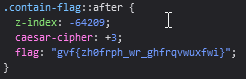
Since this flag property looks nothing like CSS, it’s a safe bet to assume this is the answer to the challenge, but upon pasting the text into the answer box I am told that this answer is incorrect. Looking back at the CSS, it’s now time to consider this caesar-cipher. So I searched for a caesar-cipher decoder website so that I can find the answer faster than doing it by hand. The shift I assume to be three, and even if there was no way to determine the shift the answer space is small enough to brute force.
The resulting string is accepted by the site (after a little fiddling with it) and that’s the first flag.
Where I Struggled
In the next challenge I was sent to another site, this time I was searching for an admin page on the website. So I clicked through all the links and found nothing. My next step was to search the sitemap and robots.txt (this was based on a hint that no search engine could find the admin page). The sitemap was not found, but the robots.txt file showed there were two paths that were disallowed- the first was for the JS and CSS code for the site, but the other was a blank page that said admin. Upon further inspection of the source it was clear that there were two hidden fields on the page- a username and a password. There was also an action that led to another page, but when I tried to navigate to that page I was given an error that showed that my method was not allowed. Upon further inspection of the source code I found that the only HTTP method allowed was Post; my next move was to go to the terminal and use a cURL command to try to see the contents of this next page. The results of my HTTP Post to this hidden page was that I was returned a token which said, “YOU LIED TO ME !!!” I was unable to find how I could leverage this token to move forward, and I could not figure out any other clues as to how I could advance.
Next Steps
Most of the knowledge I leveraged for this CTF came from completing rooms on TryHackMe, so I plan to return to THM and keep solving rooms. I also looked into a couple of the cryptography challenges and was completely overwhelmed, it’s clear that I need to do a lot more research before I’m able to even start on those.